HR should lead the data privacy revolution
For better (and sometimes worse) technological advances over the past 10-15 years have created an almost unimaginable snowball of enterprise data. In Human Resources this pertains largely to people data and compliance reporting. Although many companies maintain policy documents for data and document retention timeframes they seem to be rarely strictly enforced. In addition the rate at which governments pass data privacy laws in individual countries is making the job of HR master data and document management even more complex, especially for global companies.
HR itself is often considered “overhead” or simply a cost center. However, in the current environment through both growth of people data and security risk the HR group is well positioned to lead the transformation of an organization around data privacy.
Human Resources for many years has lamented the lack of strategic influence on the organizations they serve. There has never before been an issue like data privacy that garners the attention of the board and executive levels of an organization so universally across all industries, company sizes and geographies.
HR already has responsibility for the most sensitive data organizations protect
Workforce systems are a high value hacking target being loaded with very sensitive personal data including but often vastly exceeding data elements below;
- Full names
- Social IDs
- Home addresses
- Children’s names and socials
- License numbers, passport information
- and much more…
HR application landscapes are ridden with redundant, ageing web-based and mobile employee portals which often provide predictable openings to hackers for phishing scams, application vulnerabilities, and even the internal bad actor. This data also has a “long” risk because it rarely if ever changes. Payment data (cards, bank accounts, payment app information, etc.) can be changed if breached, personal data is good for years to continue to exploit well beyond a one-time breach discovery. You can’t change your name and social security realistically – it’s one and done.
Business functions like HR should not assume “data privacy” is the role of IT. Nor is it the same as “cybersecurity”.
Cybersecurity is the role of IT in preventing external access to the network and assets, Data Privacy is the role of the Business function in restricting application data access and should be designed based on the assumption that cybersecurity measures have already failed or will eventually.
HR has the ability not only to manage analytics for its own datasets, but also to provide dimensions to all aspects of analytics related to the individual. For example analytics related to cybersecurity incidents can be coupled with organizational data for very deep insights. This can answer questions not possible to answer easily before;
Geographically where are incidents occurring by country, office location or region?
What business functions pose the highest risks for security and privacy?
Are terminated or high risk individuals (contractors, subcontractors) still accessing sensitive data systems?
Challenges and Trends
- Accelerating Data Proliferation (more systems, more connected devices, bigger enterprise appetite for data)
- Increasing Identity theft and hacking incidents
- Global legal complexity regarding data protection and data privacy
- Strategic move to cloud platforms often presents risks to data ownership.
- GDPR, CCPA, etc have specific data subject rights to enforce and accommodate
How does Fuse help?
- Identification of PII (Personally Identifiable Information) in data and documents.
- Tagging of documents and data with retention policy rules
- Consolidation and Security of legacy and current data and documents
- End to end PII lifecycle management from import to purging of data and documents
- Manage Personal data for terminated employees, enable data portability GDPR requirements, right to be forgotten requests.
Data Retirement / PII Lifecycle
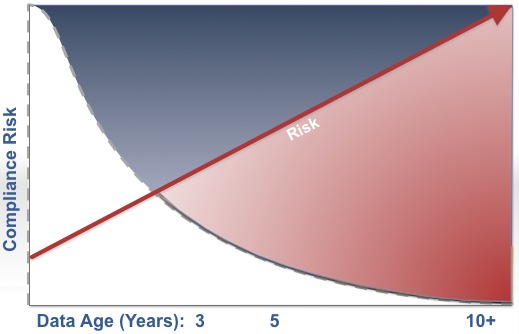
Risk exposure of data is a function of volume (# of records), time accessible, and frequency accessed. It is complicated by the fact that individual countries are passing laws to limit data privacy risk and data retention faster than many companies and HR departments can adapt.
In the U.S. laws are often directed at minimum retention periods whereas in EU nations the laws are typically more limiting to maximum retention periods. This results in a complex data life cycle strategy for organizations where rules must be enforced for physical purging of certain data and documents typically based on an employee’s citizenship and/or work location.
The graph represents the data life cycle specifically in HRIS systems today. Most regulatory reports, customer reports, and interfaces pull data only through the last 3 years of history while the older data remains idle in the system(s) without Analytics applications in place.
The average HRIS has a lifespan of 7-10 years. This results in 60-80% of the data (data that is greater than 3 years in age) sitting mostly unused for any reporting, but still facing even more risk than active data.
Unfortunately, because the data is viewed as “history” it is often dumped into data warehouses and unsecured databases since implementation partners and IT departments will not convert full history into transactional systems due to the additional workload and cost. In many cases the improvised security is insufficient to protect PII (Personally Identifiable Information). Often, users and corporate compliance departments are unaware of the underlying technical exposure.